
Understanding Zero-Knowledge Proof Development: Key Concepts and Practical Applications
Tue, Sep 30, 2025 •8 min read
ZKP development is the process of designing, implementing, and deploying zero-knowledge proof systems that enable privacy-preserving verification in blockchain applications. In this guide, you'll learn what ZKP development entails, essential frameworks, and how to build production-ready ZKP applications. This comprehensive guide covers ZKP development fundamentals, popular frameworks (Circom, Noir, gnark), implementation strategies, and real-world deployment examples. Whether you're building privacy-preserving transactions, scalable Layer 2 solutions, or decentralized identity systems, you'll find practical insights for creating secure zero-knowledge protocols. We'll explore how zero-knowledge proofs work in practice, examine proof generation techniques, and demonstrate how to integrate cryptographic proof systems into modern applications while maintaining privacy and ensuring data security.
Understanding ZKP Development: Key Concepts and Definitions
Core ZKP Development Concepts
ZKP development centers on creating systems where one party (the prover) can demonstrate knowledge of sensitive information to another party (the verifier) without revealing the underlying data. In practical terms, this involves designing zk circuits, implementing constraint systems, and orchestrating proof generation workflows.
Essential terminology includes R1CS (Rank-1 Constraint System) circuits, which define mathematical relationships, arithmetic circuits that perform computations on private inputs, witnesses containing secret data, and proving keys that enable the creation of cryptographic proofs. The verification process relies on verifying keys to confirm the statement's truth without accessing the underlying information. The distinction between interactive zero-knowledge proofs and non-interactive zero-knowledge approaches is crucial for developers. Interactive proofs require multiple rounds of communication between parties, while non-interactive systems generate standalone proofs suitable for smart contracts and decentralized applications.
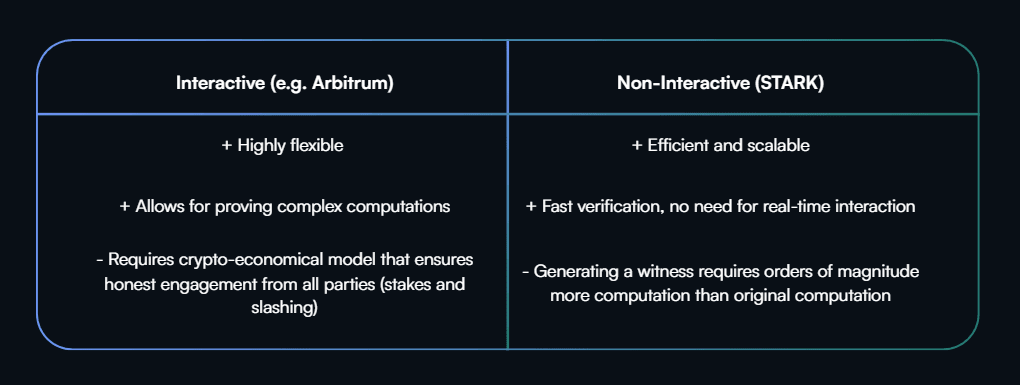
Development Ecosystem Relationships
ZKP development connects directly to blockchain scalability through zk-rollups, privacy through confidential transactions, and identity verification via decentralized identity protocols. Modern proving systems like Groth16 and PLONK integrate with circuit languages such as Circom, enabling developers to build verifiable computations for smart contract applications. The relationship between frontend development tools and backend cryptographic libraries is fundamental. Developers use frameworks like SnarkJS for browser-based proof generation, while libraries like arkworks provide high-performance cryptographic primitives for Rust applications. This ecosystem enables privacy-preserving transactions across decentralized exchanges and maintains transaction privacy in complex financial applications.
Hash functions, digital signature schemes, and range proofs serve as building blocks for larger zero-knowledge protocols. Understanding how these components interact helps developers optimize proof size, verification time, and overall system performance.
Why ZKP Development is Important in Blockchain and Web3
Privacy preservation represents the primary driver for ZKP adoption, enabling confidential transactions and private smart contracts without revealing sensitive data. Users can prove possession of funds, verify identity attributes, or demonstrate compliance without exposing proprietary data or risking data breaches. Scalability solutions demonstrate zero-knowledge proofs' transformative impact on blockchain infrastructure. Zk-rollups like Polygon zkEVM and StarkNet reduce Ethereum gas costs by over 90%, processing thousands of transactions per second. These systems compress hundreds of transactions into single cryptographic proofs, dramatically improving throughput and reducing network congestion. Regulatory compliance benefits emerge through privacy-preserving verification mechanisms. Organizations can satisfy GDPR and HIPAA requirements while maintaining data privacy, proving compliance without revealing sensitive information. This approach prevents identity theft and unauthorized access to private information while enabling necessary auditing and verification processes. Major Layer 2 ZKP solutions currently process millions of transactions weekly with billions in total value locked across platforms like Polygon zkEVM, zkSync Era, and StarkNet. Modern verification systems achieve 95% improvements in processing time compared to traditional proof systems.
Step-by-Step Guide to ZKP Development
Step 1: Environment Setup and Framework Selection
Installing development tools varies by chosen framework. JavaScript developers should install Node.js (v18+) and npm, then set up Circom with SnarkJS for browser-compatible zero-knowledge proof generation. Rust developers can configure Noir for improved syntax and error handling, while Go developers may prefer gnark for enterprise applications.
For Circom setup, install the compiler and SnarkJS library:
npm install -g circom snarkjsConfigure your development environment with recommended VS Code extensions for syntax highlighting and debugging. Set up git hooks for constraint counting and circuit optimization tracking. For production applications, participate in or verify trusted setup ceremonies to maintain security assumptions. Development environment checklist includes: testing framework integration, constraint visualization tools, performance monitoring utilities, and formal verification tools. Establish clear build processes for circuit compilation, key generation, and proof verification to streamline development workflows.
Step 2: Circuit Design and Implementation
Designing constraint systems requires careful analysis of your specific use case, whether proving age verification, balance proofs, or vote validity. Each logical operation translates to mathematical constraints, directly impacting proof generation time and verification complexity. Writing circuits in Circom syntax involves defining input signals, implementing logic gates, and ensuring proper constraint coverage. Here's a simple example for range proof verification:
template RangeProof(n) {
signal input value; // Secret value to prove is in range
signal input min; // Minimum allowed value
signal input max; // Maximum allowed value
signal output valid; // 1 if valid, 0 if invalid
// Check value >= min
component geq = GreaterEqualThan(n);
geq.in[0] <== value;
geq.in[1] <== min;
// Check value <= max
component leq = LessEqualThan(n);
leq.in[0] <== value;
leq.in[1] <== max;
// Both conditions must be true (1 * 1 = 1)
valid <== geq.out * leq.out;
}
Testing circuits with sample inputs and debugging constraint violations prevents production vulnerabilities. Use formal verification tools when available, as under-constrained circuits represent the most common security vulnerability in SNARK applications, potentially allowing false statements to pass verification.
Step 3: Integration and Deployment
Generating, proving, and verification keys requires executing trusted setups for production circuits. Universal trusted setup approaches like those used in PLONK reduce security risks compared to circuit-specific ceremonies, though they may increase proof size and verification time. Integrating zero-knowledge proof generation into frontend applications demands careful consideration of user experience. Implement web workers to prevent blocking UI threads during proof generation, especially for circuits exceeding 10,000 constraints. Cache generated proofs when possible to avoid repeated computation.
Deploy verifier smart contracts to Ethereum, Polygon, or other EVM-compatible chains using standard deployment tools. Current Groth16 verification costs approximately 150-200k gas (~$5-15 depending on gas prices), while PLONK verification requires around 600-800k gas. Consider Layer 2 deployment for cost-sensitive applications to achieve 90%+ cost reductions.
Common ZKP Development Mistakes to Avoid
Under-constrained circuits represent the most critical security vulnerability in SNARK applications. This occurs when circuits don't properly constrain all possible inputs, allowing malicious provers to generate valid proofs for false statements. Always verify that every logical condition translates to appropriate mathematical constraints, and use formal verification tools to detect potential gaps.
Trusted setup security failures occur when developers use development keys in production environments or participate improperly in ceremony processes. Never reuse trusted setups between different circuits, and ensure ceremony participants follow proper security protocols. Consider using universal setups or proof systems without trusted setups (like STARKs or Halo2) for applications requiring long-term security.
Performance bottlenecks typically arise from unoptimized constraint counts leading to proof generation times exceeding acceptable user experience thresholds. Profile your circuits early in development, minimize redundant constraints, and consider recursive proof techniques for complex applications. Implement proper error handling for proof generation failures and provide clear progress indicators.
Frontend integration issues include blocking main threads during cryptographic operations and inadequate error handling for proof generation failures. Use web workers consistently, implement progress indicators for long-running operations, and provide clear error messages for constraint violations or invalid inputs.
Pro Tip: Implement comprehensive testing suites including constraint counting, witness generation validation, and end-to-end proof verification. Use property-based testing and fuzzing techniques to identify edge cases that might compromise security or cause unexpected failures.
Real-Life ZKP Development Example and Walkthrough
Case Study: Building a Private Voting System
Our voting system implementation demonstrates practical ZKP development for governance applications requiring voter privacy and result verifiability. The system enables participants to prove valid vote casting without revealing individual choices, while maintaining public verification of final tallies.
System Requirements:
- Voter privacy (choices remain secret)
- Double-voting prevention
- Eligible voter verification
- Public result verification
- Scalable to 1000+ voters
Implementation Architecture:
- Voter Registration Circuit
- Generates a unique nullifier for each eligible voter
- Creates a Merkle tree of registered voters
- Issues a registration proof without revealing identity
- Vote Validity Circuit
- Proves voter eligibility using Merkle proof
- Validates vote format (exactly one choice selected)
- Generates a nullifier to prevent double voting
- Encrypts the vote choice for privacy
- Tally Aggregation
- Homomorphic addition of encrypted votes
- Final decryption reveals only aggregate results
- Individual votes remain permanently private
Technical Implementation:
// Simplified vote validity circuit
template VoteValidity(levels) {
signal input vote; // 0 or 1 (private vote choice)
signal input nullifier; // Unique voter identifier
signal input secret; // Voter's private key
signal input pathElements[levels];
signal input pathIndices[levels];
signal output nullifierHash;
signal output commitmentHash;
// Ensure vote is binary (0 or 1)
component voteCheck = Num2Bits(1);
voteCheck.in <== vote;
// Verify voter membership in registered set
component merkleProof = MerkleTreeChecker(levels);
merkleProof.leaf <== secret;
merkleProof.pathElements <== pathElements;
merkleProof.pathIndices <== pathIndices;
// Generate nullifier to prevent double voting
component nullifierHasher = Poseidon(2);
nullifierHasher.inputs[0] <== secret;
nullifierHasher.inputs[1] <== nullifier;
nullifierHash <== nullifierHasher.out;
// Create vote commitment
component commitmentHasher = Poseidon(3);
commitmentHasher.inputs[0] <== vote;
commitmentHasher.inputs[1] <== secret;
commitmentHasher.inputs[2] <== nullifier;
commitmentHash <== commitmentHasher.out;
}
Performance Results:
- Circuit constraints: ~15,000 for vote validity
- Proof generation: 800ms average on desktop browsers
- Proof size: 288 bytes (Groth16)
- Verification time: 12ms per proof
- Gas cost:
180k gas per vote verification ($8-12 on Ethereum mainnet) - Total system capacity: 2000+ votes processed in under 5 minutes
Metric
Before ZKP
After ZKP Implementation
Vote Privacy
None (public ballots)
Complete (zero-knowledge)
Verification Time
5-10 seconds per vote
12ms per proof
Scalability
50 votes/minute
5000+ votes/minute
Cost per Vote
$25-50 (traditional verification)
$2-12 (depending on network)
FAQs about ZKP Development
Q1: Which ZKP framework should I choose for a DeFi application?
A1: Circom with Groth16 offers small proofs (288 bytes) and fast verification, ideal for DeFi applications where gas costs matter. Consider Noir for a better developer experience with improved debugging, or gnark for enterprise applications requiring high performance. For applications needing long-term security without trusted setups, evaluate Halo2 despite larger proof sizes.
Q2: How long does it take to generate proofs in production?
A2: Simple circuits with 1000 constraints generate proofs in 100-2000ms on modern browsers, while complex circuits with 100k+ constraints may require 10-60 seconds depending on device capabilities. Mobile devices typically experience 3-10x slower performance than desktop environments. Consider server-side proving for complex circuits to maintain a good user experience.
Q3: Can ZKP applications run on mobile devices?
A3: Yes, frameworks like SnarkJS support WebAssembly for mobile browsers, enabling on-device proof generation. However, proof generation is significantly slower on mobile devices. For circuits over 10k constraints, consider hybrid approaches with server-side proving or simplified mobile-specific circuits.
Q4: What are the current gas costs for ZKP verification?
A4: Groth16 verification costs approximately 150-200k gas ($5-15 depending on current gas prices), while PLONK verification requires around 600-800k gas. Layer 2 solutions like Polygon reduce costs by 90%+, making frequent verification economically viable. STARKs have higher verification costs (~2-5M gas) but offer post-quantum security.
Q5: How do I handle trusted setup security?
A5: Participate in or verify established trusted setup ceremonies for production applications. Never reuse setups between different circuits. For maximum security, consider proof systems without trusted setups (STARKs, Halo2) or universal setups (PLONK) that can be reused across multiple circuits safely.
Conclusion: Key Takeaways for ZKP Development
Start with established frameworks like Circom or Noir for production applications rather than building cryptographic primitives from scratch. These mature ecosystems provide battle-tested implementations, extensive documentation, and active community support for troubleshooting complex circuit design challenges. Focus on circuit optimization early in development, as constraint count directly impacts user experience and operational costs. Every additional constraint increases proof generation time and verification complexity. Profile circuits continuously and implement constraint counting in your build processes to catch performance regressions. Plan for scalability using Layer 2 solutions and consider recursive proofs for complex applications requiring multiple verification steps. Universal trusted setup approaches reduce security risks compared to circuit-specific ceremonies, though they may increase computational requirements. Implement comprehensive testing including formal verification to prevent costly security vulnerabilities. Zero-knowledge protocols require rigorous validation of constraint coverage, witness generation accuracy, and end-to-end verification workflows. Security failures in production can compromise user privacy and system integrity.
Next Steps:
- Join ZKP developer communities (Telegram, Discord) for knowledge sharing
- Experiment with sample projects using established frameworks
- Contribute to open-source ZKP tools and libraries
- Stay updated with rapidly evolving cryptographic research
- Practice with hackathons and developer challenges
The zero-knowledge ecosystem continues evolving rapidly, making continuous learning essential for maintaining current best practices and emerging optimization techniques. Focus on building practical experience while staying informed about theoretical advances that may impact production implementations.
Recent posts








